Netbook computers are dead by Windows 8
Posted on September 12, 2012 by Kara Dunlap in Blog

Netbook computers are formally dead, and Home windows 8 drawn the trigger
by Kaira Chacos, digitaltrends.com
September seventh 2012

Pills might have left netbook computers bloody and beaten, however it was Home windows 8 that did the dirty work of extinguishing the small laptops permanently.
Researchers crowded round the small, lifeless husk lounging shattered in the pub before them. The morning sun glistened off a cracked 10-inch display damaged chips and transistors littered the floor like a lot of spent pennies. Sounds of revelry echoed from somewhere far because the townsfolk celebrated a vibrant future filled with pills, phablets and easily charging phones, not aware from the dying within their midst.
One investigator kneeled lower and depressed the gadget’s energy button. Three seconds later, a blue screen of death of dying gradually faded to black around the damaged screen.
“It’s official,” the guy stated. “The netbook computer is dead.”
“I think we all know who accounts for this,” certainly one of his co-workers responded. “I’ll start carrying pills lower towards the station for questioning.”
“Not so quick,” the very first investigator stated. He gradually was. “Bring me Home windows 8.”
The finish of the era
Netbook computers have been receiving existence support for some time now. Previously year, Dell and Toshiba formally bowed from the market, while Lenovo’s S-series netbook computers have been receiving-again, off-again, but mostly off-again. (They’re presently available included in a restricted-time offer, probably to drum up curiosity about their new, full-sized S-series choices.) In May, the Canalys research firm introduced that netbook computer sales dropped for that sixth consecutive quarter, by an astonishing 34 percent in comparison to the year before.
Two companies remained in keeping with the very first ultra-portable form factor through all of the disaster and gloom: Acer and Asus. But no more. Both companies intend on tugging the plug on netbook computers, DigiTimes reviews.
Acer has yet to formally read the report, but nonetheless, Asus’ withdrawal signifies the dying blow. Asus created the very first computer to hold the netbook computer title — the initial Eee PC — and ongoing delivering netbook computers faithfully since. So far, that’s.
What motivated Asus to snuff out its very own offspring? The muse appears straightforward initially: Asus Boss Jerry Shen told DigiTimes that the organization “plans to possess its Transformer tablet Computers fill the ten-inch mobile phone market, changing its netbook computer products.”
Just like any good murder mystery, however, things aren’t as easy as they appear.
Pills: Perp or patsy?
An upswing of pills left netbook computers bruised, battered and spinning. It’s difficult to ignore the truth that netbook computer sales began their gargantuan nose dive virtually the precise moment the original iPad was introduced this year. Netbook computers are slow and frumpy pills are responsive and sexy. To complicate matters, Home windows never really fit well on the 10-inch screen, while tablet os’s specified for around tinier shows. Frankly, it’s no shocker the mainstream has diverted its attention from netbook computers to pay attention to pills.
The netbook computer form factor still holds some value in certain niche uses. For example, business vacationers with heavy workloads often lean towards portable Computers with physical keyboards. This Feb, Asus marketing Vice president Kevin Huang told PCWorld that “Asus produced the netbook computer category, and i believe netbook computers today still supply the most cost-effective computing product solution maintenance certain user segments–i.e., the K-12 education market.”
An effective investigator perks his ears up when someone shows an abrupt alternation in behavior. Why did Asus change its tune so significantly in this small amount of time?
The DigiTimes report states it had been because of “a sharp drop sought after in emerging marketplaces,” among the last bastions of netbook computer growth. I only say hogwash: Home windows 8 drove the ultimate nail in to the netbook’s coffin.
Home windows 8: Microsoft kills the netbook computer
Producers battled to earn money with netbook computers in the very best of occasions despite low-finish processors along with a small, low-resolution screen, it’s hard to earn money on the PC which will only cost $200 to $350 at retail.
Actually, screen resolutions might be one of the leading factors within the dying from the netbook computer. Most notebook computers stay with a 1024 x 600 display Home windows 8 requires 1024 x 768 at least. You’ll need a full 1366 x 768 resolution (seen of all mainstream laptops in dimensions as much as 15.6-inches) to make use of the operating system’s snap feature.
Display costs have a large slice of a laptop’s overall component costs. Producers who’ve been in a position to draw some slim profits from netbook computers could be in over their heads when they add greater-cost, greater-resolution shows to goad Home windows 8 into focusing on the pint-sized PCs… and it is not even counting the price of improving to touchscreens to make the most of Home windows 8′s finger-friendly features, something pills sport automatically.
 Heaping on much more expense, certification costs for Home windows RT are rumored to become $50 to $100, with respect to the version, without any low-cost same as the Home windows 7 Starter edition available on a lot of netbook computers being offered. Compare that towards the cost from the open-source Android Operating System that forces a lot of pills: $. To become fair, several producers pay Microsoft a certification fee for every Android device they create to prevent possible patent lawsuit — but Asus isn’t one of these.
Heaping on much more expense, certification costs for Home windows RT are rumored to become $50 to $100, with respect to the version, without any low-cost same as the Home windows 7 Starter edition available on a lot of netbook computers being offered. Compare that towards the cost from the open-source Android Operating System that forces a lot of pills: $. To become fair, several producers pay Microsoft a certification fee for every Android device they create to prevent possible patent lawsuit — but Asus isn’t one of these.
Meanwhile, all of the spiritual successors to netbook computers yield greater margins for producers: Ultrabooks, tablet-notebook hybrid cars, and low-cost ultrathin laptops. Producers won’t ever have the ability to create make money from sheer netbook computer sales volumes again. Trading in Home windows 8 and it is greater-costing display needs just doesn’t seem sensible.
Considering evidence, the reason is obvious: pills and shifting consumer desires might have left netbook computers inside a critical condition, however it was Home windows 8 that wiped out the netbook computer off permanently. Moore’s law is really a cruel mistress indeed.
Situation CLOSED!
Original Page: http://world wide web.digitaltrends.com/computing/netbook computers-are-formally-dead-and-home windows-8-drawn-the-trigger/
Remove Recovery virus
Posted on September 6, 2012 by Kara Dunlap in Blog

Remove Recovery virus
by Stelian Pilici, malwaretips.com
This summer thirteenth 2012
Recovery is really a malicious program which will display fake alerts, declaring that several hard disk errors and computer issues were detected in your machine.
The truth is, no reported issues are really the, and therefore are only accustomed to scare you into buying Recovery and stealing your individual financial information.
Aside from the bogus alerts and warning,this rogue software has transformed your desktop background to some solid dark colored,has hidden your files and folders and it is leading to browser redirects.
Included in its self-defense mechanism,Recovery has disabled the Home windows system utilities, including Task Manager and Home windows Registry and it is block you against running certain programs that can lead to its removal.
In case your computer is have contracted Recovery virus,then you’re seeing this images:



We strongly counsel you to follow along with our Recovery virus removal guide and ignore any alerts this malicious software might generate.
Under no circumstance in the event you buy this rogue security software because this can lead to id theft,and when you’ve, you need to speak to your charge card company and dispute the charge proclaiming that this program is really a scam along with a trojan.
Registration codes for Recovery
Being an optional step,you should use the next license answer to register Recovery virus and prevent the fake alerts.
Recovery activation code: 56723489134092874867245789235982
Please bear in mind that entering the above mentioned registration code will NOT remove Recovery out of your computer , rather it’ll just stay away from the fake alerts to ensure that you’ll have the ability to complete our removal guide easier.
Recovery Removal Instructions
The 1st Step : Start your pc in Safe Mode with Networking
- Remove all diskettes, Compact disks, and Dvd disks out of your computer, after which restart your pc.
- Press and contain the F8 key as the computer restarts.Please bear in mind you need to press the F8 key prior to the Home windows start-up logo design seems.
Note: With a few computer systems, should you press and hold a vital because the computer is startup you’re going to get a stuck key message. If the happens, rather than pressing and holding the “F8 key”, tap the “F8 key” continuously before you obtain the Advanced Boot Options screen. - Around the Advanced Boot Options screen, make use of the arrow secrets to highlight Safe Mode with Networking , after which press ENTER.

Step Two: Remove Recovery malicious proxy server
Recovery will add a proxy server which prevents the consumer from being able to access the web,adhere to the below instructions to get rid of the proxy.
- Start the web Explorer browser and when you use Ie 9 ,click the gear icon (Tools for Ie 8 customers) ,then choose Internet Options.
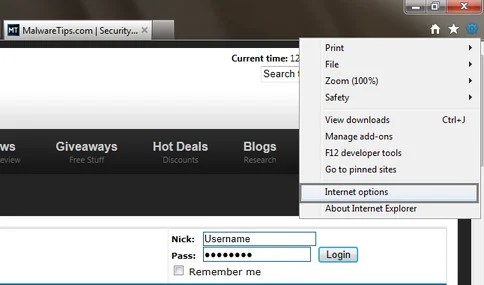
- Visit the tab Connections.At the end, click LAN configurations.
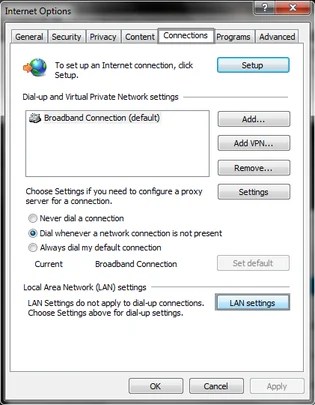
- Uncheck the choice Make use of a proxy server for the LAN. This will take away the malicious proxy server and permit you to search on the internet again.
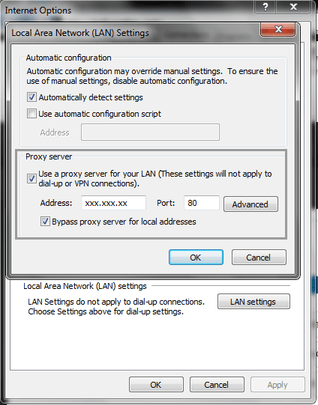
If you’re a Opera customers, visit Opera(upper left corner) → Options → Advanced tab → Network → Configurations → Choose No Proxy
Step Three: Run RKill to terminate known adware and spyware processes connected with Recovery.
RKill is really a program which will make an effort to terminate all malicious processes connected with Recovery virus,to ensure that we’ll have the ability to perform the next phase without having to be interrupted with this malicious software.
As this utility is only going to stop Recovery running process, and doesn’t remove any files, after running it you shouldn’t reboot your pc just like any adware and spyware processes which are set up to begin instantly will you need to be began again.
- While your pc is within Safe Mode with Networking ,please download the most recent official sort of RKill.Please be aware that we’ll make use of a re-named sort of RKILL to ensure that Recovery won’t block this utility from running.
RKILL DOWNLOAD LINK (This link will instantly download RKILL re-named as iExplore.exe) - Double-click the iExplore.exe icon to be able to instantly make an effort to stop any processes connected with Recovery.

- RKill will begin working without anyone’s knowledge, be patient as the program searches for various adware and spyware programs and attempts to terminate them.
IF you’re getting problems beginning or running RKill, you are able to download every other re-named versions of RKill came from here. - When Rkill has completed its task, it’ll produce a log. After that you can proceed using the relaxation from the guide.
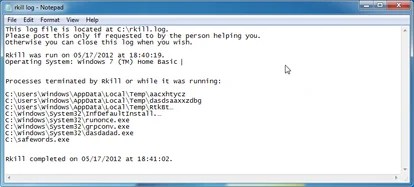
WARNING: Don’t reboot your pc after running RKill because the adware and spyware process will begin again , stopping you against correctly carrying out the next phase.
Step Four: Remove Recovery malicious files with Malwarebytes Anti-Adware and spyware FREE
- Download the most recent official sort of Malwarebytes Anti-Adware and spyware FREE.
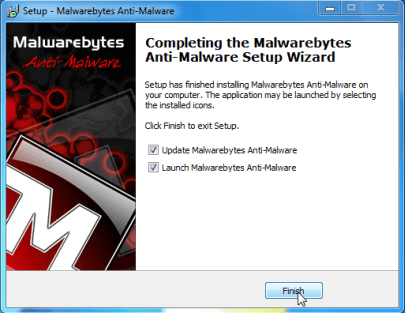
MALWAREBYTES ANTI-Adware and spyware DOWNLOAD LINK (This link will open a download page inside a new window from where one can download Malwarebytes Anti-Adware and spyware Free) - Start the Malwarebytes’ Anti-Adware and spyware installation process by double hitting mbam-setup file.

- Once the installation starts, keep following a prompts to be able to follow the setup process. Don’t make any changes to default configurations so when this program has finished setting up, make certain you depart both Update Malwarebytes’ Anti-Adware and spyware and Launch Malwarebytes’ Anti-Adware and spyware checked. Then click the Finish button. If Malwarebytes’ prompts you to definitely reboot, don’t achieve this.
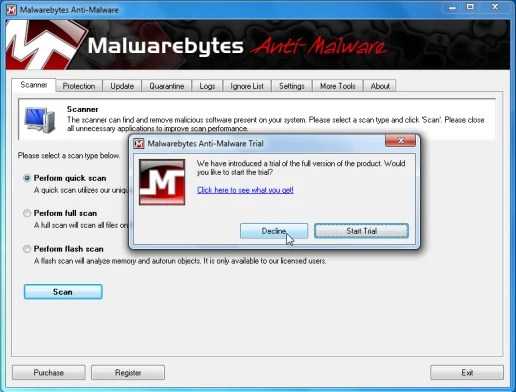
- Malwarebytes Anti-Adware and spyware will start and you will be motivated to begin an effort period , please choose ‘Decline‘ once we would like to make use of the on-demand scanner.
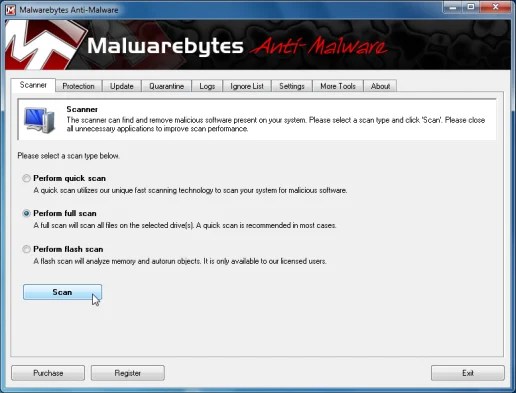
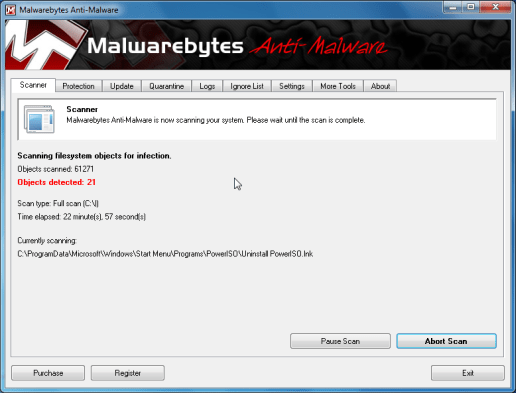
- Around the Scanner tab,choose Perform full scan after which click the Scanbutton to begin checking your pc.
- Malwarebytes’ Anti-Adware and spyware will start checking your pc for Recovery malicious files as proven below.
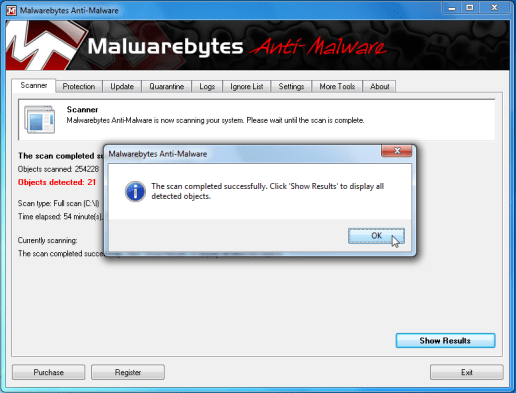
- Once the scan is completed a note box can look, click OK to carry on.
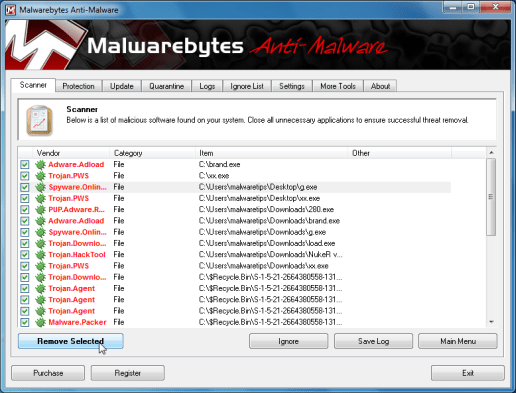
- You’ll certainly be given a screen demonstrating the adware and spyware infections that Malwarebytes’ Anti-Adware and spyware has detected.Please be aware the infections found might be diverse from what’s proven within the image.Make certain that things are Checked (ticked) and then click the Remove Selected button.
- Malwarebytes’ Anti-Adware and spyware will start getting rid of the malicious files.After finishing this it’ll display a note proclaiming that it must reboot,please allow this request after which give your PC boot in Normal mode.
Step Five: Make sure the body for just about any remaining infections with HitmanPro
- This task could be carried out in Normal Mode ,so please download the most recent official sort of HitmanPro.
HITMANPRO DOWNLOAD LINK (This link will open a download page inside a new window from where one can download HitmanPro) - Double click the formerly downloaded fileto begin the HitmanPro installation.

IF you’re going through problems while attempting to beginning HitmanPro, you should use the “Pressure Breach” mode.To begin the program in Pressure Breach mode, hold lower the left Control-key when you begin HitmanPro and all sorts of non-essential processes are ended, such as the adware and spyware process. (How to begin HitmanPro in Pressure Breach mode – Video) - Click Next to set up HitmanPro in your system.
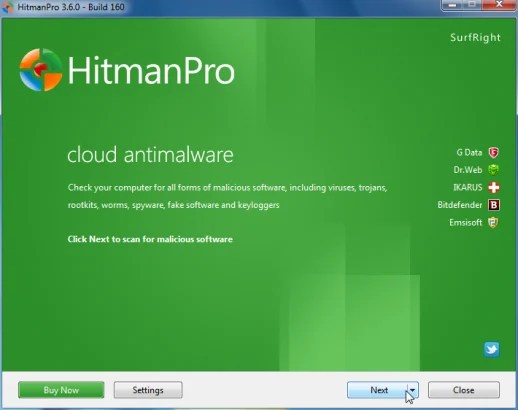
- The setup screen is displayed, from which you’ll decide whether you want to set up HitmanPro in your machine or simply execute a one-time scan, choose a option then click Next to begin a method scan.
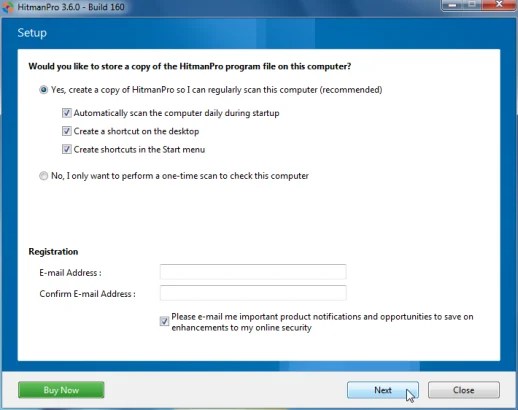
- HitmanPro will begin checking the body for malicious files as observed in the look below.
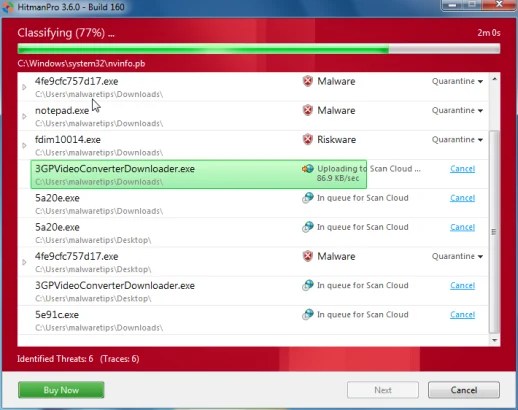
- When the scan is finished,you will visit a screen that will display all of the malicious files the program finds.Click on on Next to get rid of this malicious files.
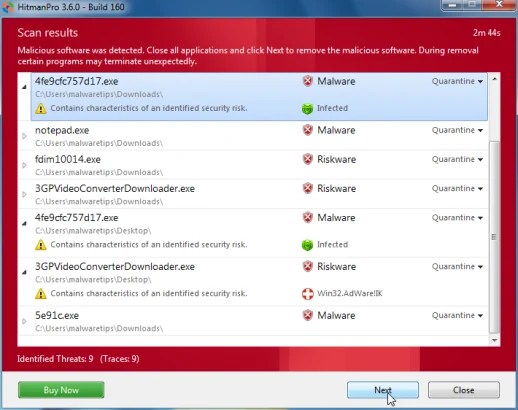
- Click Activate free license to begin the disposable thirty days trial and take away the malicious files.

- HitmanPro will start getting rid of the infected objects.If the program will request you to definitely restart your pc,make sure you allow this request.
Step Six : Reinstate your cutting corners and take away any remaining malicious registry secrets
Recovery has moved your cutting corners files within the Temporary Internet folder and added some malicious registry secrets for your Home windows installation , to revive your files we will have to execute a scan with RogueKiller.
- Please download the most recent official sort of RogueKiller.
ROGUEKILLER DOWNLOAD LINK (This link will instantly download RogueKiller on your pc) - Double click RogueKiller.exe to begin this utility after which wait for a Prescan to accomplish.This will take merely a couple of seconds and you can click on the Start button to carry out a system scan.

- Following the scan has completed, press the Remove button to get rid of any malicious registry secrets.

- Next we will have to reinstate your cutting corners, so click the ShortcutsFix button and permit this program to operate.

STEP 7: Unhide your files and folders
Recovery modifies your file system in a way that files and folders become hidden, to revive the default configurations , it’s important to run the below program.
- Download the Unhide utility, to unhide your files and folders.
UNHIDE.EXE DOWNLOAD LINK (This link will instantly download the Unhide utility on your pc) - Double-click the Unhide.exe icon on your hard drive and permit this program to operate.The entire process shouldn’t take a lot more than ten minutes to accomplish,and also at the finish this utility will produce a report.
STEP 8: Get the desktop think back!
Recovery changes your desktop background to some solid dark colored,to alter it to default one stick to the below instruction.
Original Page: http://malwaretips.com/blogs/file-recovery-virus/
Canonical launches Ubuntu One recommendations program
Posted on August 21, 2012 by Kara Dunlap in Blog


Canonical launches Ubuntu One recommendations program, allows you get cloud storage one friend at any given time
Should you’re wealthy in pals, but poor in cloud space for storage, Canonical enables you to turn individuals relations into mb using its new Ubuntu One recommendations program. Should you didn’t wish to pay before, you can get as much as 5GB of storage, by having an upgrade to 20GB readily available for $30 each year. Now, you should use the brand new link around the service’s web dash to inform your contacts about it via Twitter, Facebook or email. For every one which subscribes, you’ll have an extra 500MB, gratis, as will your recently clouded friend. However, should you’re thinking you are able to leverage that body fat Twitter list into terrabytes of off-site storage pleasure, reconsider — the limit is 40 invites, or 20GB. Still, that’s that’s pretty good in comparison towards the competition along with other referral programs, check the origin to determine how to begin.
Original Page: http://world wide web.engadget.com/2012/08/15/canonical-ubuntu-one-recommendations-program/
4 Security Training – iCloud Account Hack
Posted on August 21, 2012 by Kara Dunlap in Blog


Earlier this week, author Pad Honan had the unthinkable happen. Someone experienced his iCloud account, plus they could remotely wipe his apple iphone, iPad and Mac laptop Air and remove his Google account which was mounted on his iCloud account. The first assumption was this happened since the hacker brute-forced his distance to Honan’s account. After a little further digging, it found light the hacker was simply able to utilize social engineering to trick Apple Support into resetting his password.
Around we love to to trumpet using good passwords, this really is one instance by which this will not have designed a difference. You should use the very best password on the planet, but when someone can socially engineer you or someone in the site or service itself to show passwords, it’ll make no difference. That is not to state that strong passwords aren’t important getting a powerful password will safeguard you from nearly all common attacks. However, you should certainly not wager the farm on the password.
You will find numerous questions this raises, obviously:
- What else could you do in order to get over a catastrophic loss of data incident?
- What else could you do in order to safeguard yourself from this kind of attack?
- What’s the probability of this happening in my experience?
Honan learned the response to this primary question hard way: Make regular backup copies in multiple locations. Don’t simply depend around the Cloud to keep your backups–websites aren’t bulletproof, companies go bankrupt, problems happen. Honan may recover the accounts which were jeopardized throughout this hack, but that’s by no means certain in each and every situation. He might not have the ability to recover the year’s price of data he hadn’t supported in another location. (Though he was fortunate the remote wipe didn’t complete, so it might not be lost.)
For that second question, we’ll define the attack like a compromise on any internet account that consists of a great deal of your important data whether that become your contacts, your calendar, entire backup copies, or selected files, or simply links to numerous your other accounts (social media, banking, shopping online, etc). This may be iCloud, this may be Google, it may be a variety of different services.
We must think that you cannot trust the security of the password alone, as that may be stolen by social engineering or hacking of one other sort. But this really is another place in which a layered defense strategy is available in handy. We already covered the necessity to support your computer data in multiple places. But what else are you able to do?
- Secure because the internet data as possible.
