Remove Recovery virus
Posted on September 6, 2012 by Kara Dunlap in Blog
Remove Recovery virus
by Stelian Pilici, malwaretips.com
This summer thirteenth 2012
Recovery is really a malicious program which will display fake alerts, declaring that several hard disk errors and computer issues were detected in your machine.
The truth is, no reported issues are really the, and therefore are only accustomed to scare you into buying Recovery and stealing your individual financial information.
Aside from the bogus alerts and warning,this rogue software has transformed your desktop background to some solid dark colored,has hidden your files and folders and it is leading to browser redirects.
Included in its self-defense mechanism,Recovery has disabled the Home windows system utilities, including Task Manager and Home windows Registry and it is block you against running certain programs that can lead to its removal.
In case your computer is have contracted Recovery virus,then you’re seeing this images:



We strongly counsel you to follow along with our Recovery virus removal guide and ignore any alerts this malicious software might generate.
Under no circumstance in the event you buy this rogue security software because this can lead to id theft,and when you’ve, you need to speak to your charge card company and dispute the charge proclaiming that this program is really a scam along with a trojan.
Registration codes for Recovery
Being an optional step,you should use the next license answer to register Recovery virus and prevent the fake alerts.
Recovery activation code: 56723489134092874867245789235982
Please bear in mind that entering the above mentioned registration code will NOT remove Recovery out of your computer , rather it’ll just stay away from the fake alerts to ensure that you’ll have the ability to complete our removal guide easier.
Recovery Removal Instructions
The 1st Step : Start your pc in Safe Mode with Networking
- Remove all diskettes, Compact disks, and Dvd disks out of your computer, after which restart your pc.
- Press and contain the F8 key as the computer restarts.Please bear in mind you need to press the F8 key prior to the Home windows start-up logo design seems.
Note: With a few computer systems, should you press and hold a vital because the computer is startup you’re going to get a stuck key message. If the happens, rather than pressing and holding the “F8 key”, tap the “F8 key” continuously before you obtain the Advanced Boot Options screen. - Around the Advanced Boot Options screen, make use of the arrow secrets to highlight Safe Mode with Networking , after which press ENTER.

Step Two: Remove Recovery malicious proxy server
Recovery will add a proxy server which prevents the consumer from being able to access the web,adhere to the below instructions to get rid of the proxy.
- Start the web Explorer browser and when you use Ie 9 ,click the gear icon (Tools for Ie 8 customers) ,then choose Internet Options.
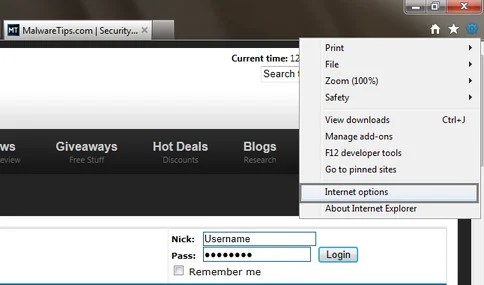
- Visit the tab Connections.At the end, click LAN configurations.
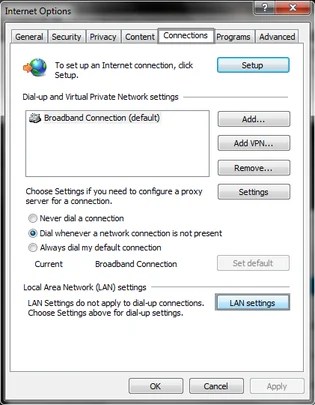
- Uncheck the choice Make use of a proxy server for the LAN. This will take away the malicious proxy server and permit you to search on the internet again.
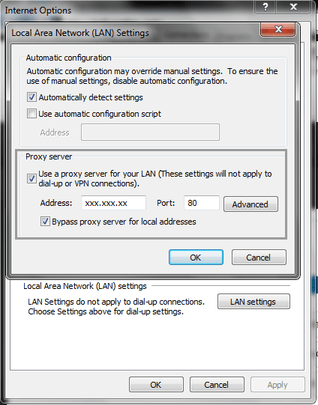
If you’re a Opera customers, visit Opera(upper left corner) → Options → Advanced tab → Network → Configurations → Choose No Proxy
Step Three: Run RKill to terminate known adware and spyware processes connected with Recovery.
RKill is really a program which will make an effort to terminate all malicious processes connected with Recovery virus,to ensure that we’ll have the ability to perform the next phase without having to be interrupted with this malicious software.
As this utility is only going to stop Recovery running process, and doesn’t remove any files, after running it you shouldn’t reboot your pc just like any adware and spyware processes which are set up to begin instantly will you need to be began again.
- While your pc is within Safe Mode with Networking ,please download the most recent official sort of RKill.Please be aware that we’ll make use of a re-named sort of RKILL to ensure that Recovery won’t block this utility from running.
RKILL DOWNLOAD LINK (This link will instantly download RKILL re-named as iExplore.exe) - Double-click the iExplore.exe icon to be able to instantly make an effort to stop any processes connected with Recovery.

- RKill will begin working without anyone’s knowledge, be patient as the program searches for various adware and spyware programs and attempts to terminate them.
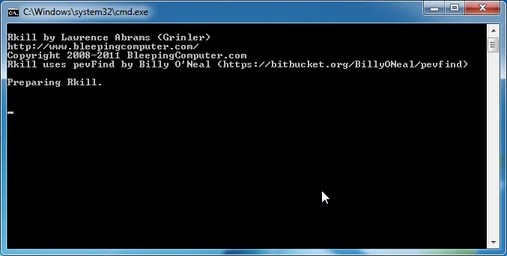
IF you’re getting problems beginning or running RKill, you are able to download every other re-named versions of RKill came from here. - When Rkill has completed its task, it’ll produce a log. After that you can proceed using the relaxation from the guide.
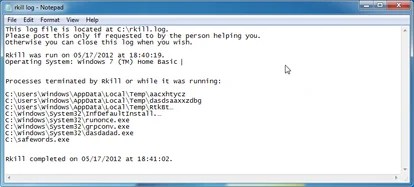
WARNING: Don’t reboot your pc after running RKill because the adware and spyware process will begin again , stopping you against correctly carrying out the next phase.
Step Four: Remove Recovery malicious files with Malwarebytes Anti-Adware and spyware FREE
- Download the most recent official sort of Malwarebytes Anti-Adware and spyware FREE.
MALWAREBYTES ANTI-Adware and spyware DOWNLOAD LINK (This link will open a download page inside a new window from where one can download Malwarebytes Anti-Adware and spyware Free) - Start the Malwarebytes’ Anti-Adware and spyware installation process by double hitting mbam-setup file.

- Once the installation starts, keep following a prompts to be able to follow the setup process. Don’t make any changes to default configurations so when this program has finished setting up, make certain you depart both Update Malwarebytes’ Anti-Adware and spyware and Launch Malwarebytes’ Anti-Adware and spyware checked. Then click the Finish button. If Malwarebytes’ prompts you to definitely reboot, don’t achieve this.
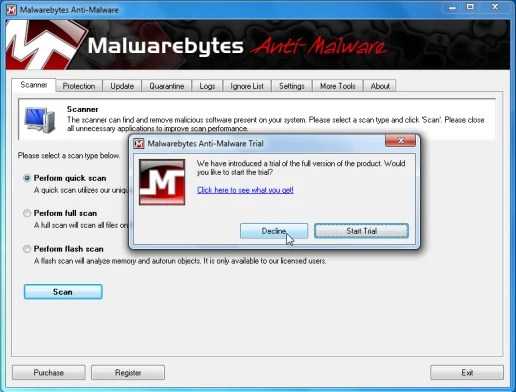
- Malwarebytes Anti-Adware and spyware will start and you will be motivated to begin an effort period , please choose ‘Decline‘ once we would like to make use of the on-demand scanner.
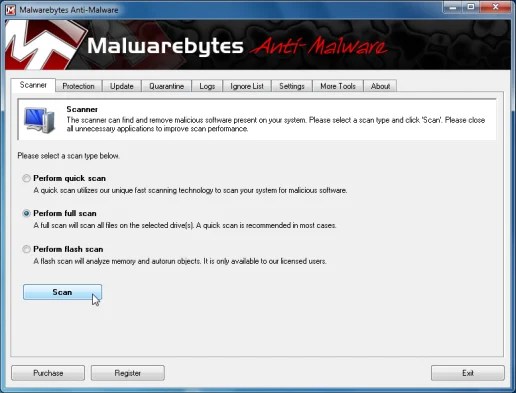
- Around the Scanner tab,choose Perform full scan after which click the Scanbutton to begin checking your pc.
- Malwarebytes’ Anti-Adware and spyware will start checking your pc for Recovery malicious files as proven below.
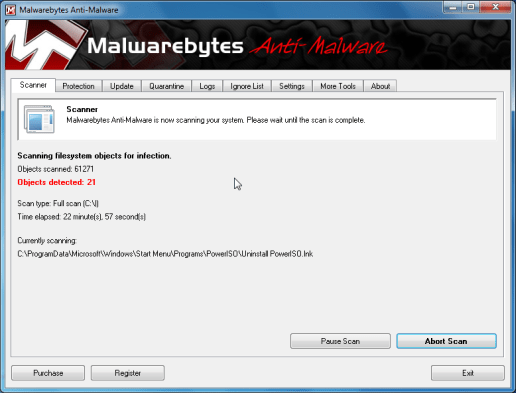
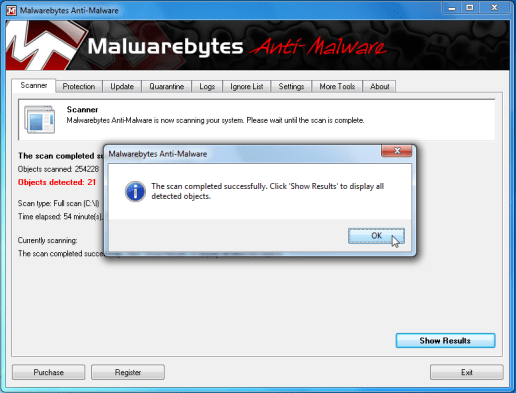
- Once the scan is completed a note box can look, click OK to carry on.
- You’ll certainly be given a screen demonstrating the adware and spyware infections that Malwarebytes’ Anti-Adware and spyware has detected.Please be aware the infections found might be diverse from what’s proven within the image.Make certain that things are Checked (ticked) and then click the Remove Selected button.
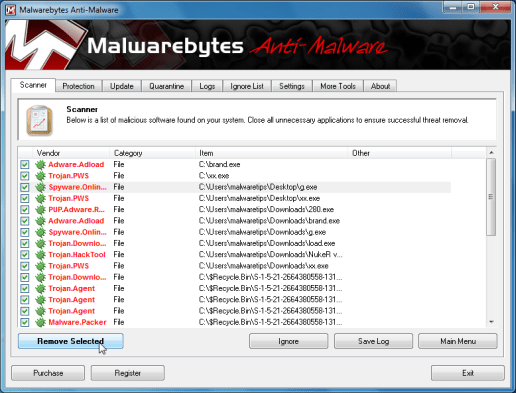
- Malwarebytes’ Anti-Adware and spyware will start getting rid of the malicious files.After finishing this it’ll display a note proclaiming that it must reboot,please allow this request after which give your PC boot in Normal mode.
Step Five: Make sure the body for just about any remaining infections with HitmanPro
- This task could be carried out in Normal Mode ,so please download the most recent official sort of HitmanPro.
HITMANPRO DOWNLOAD LINK (This link will open a download page inside a new window from where one can download HitmanPro) - Double click the formerly downloaded fileto begin the HitmanPro installation.

IF you’re going through problems while attempting to beginning HitmanPro, you should use the “Pressure Breach” mode.To begin the program in Pressure Breach mode, hold lower the left Control-key when you begin HitmanPro and all sorts of non-essential processes are ended, such as the adware and spyware process. (How to begin HitmanPro in Pressure Breach mode – Video) - Click Next to set up HitmanPro in your system.
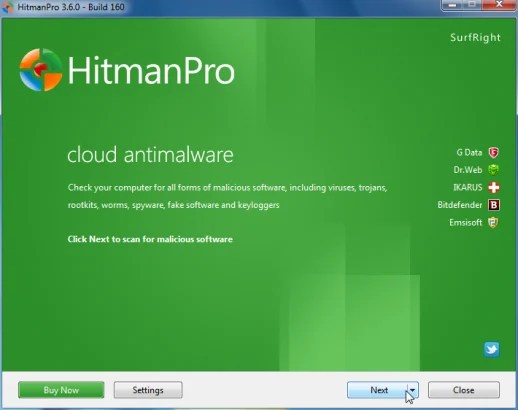
- The setup screen is displayed, from which you’ll decide whether you want to set up HitmanPro in your machine or simply execute a one-time scan, choose a option then click Next to begin a method scan.
- HitmanPro will begin checking the body for malicious files as observed in the look below.
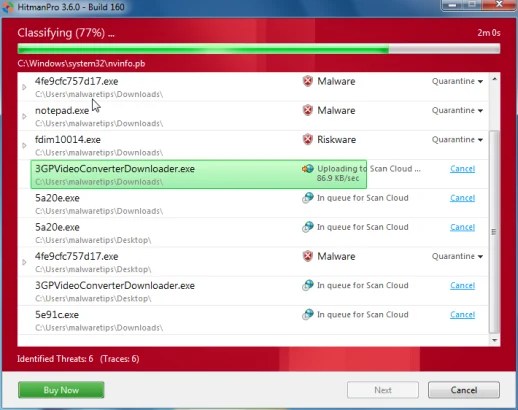
- When the scan is finished,you will visit a screen that will display all of the malicious files the program finds.Click on on Next to get rid of this malicious files.
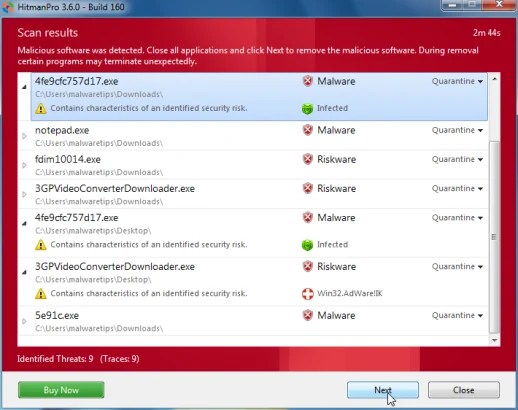
- Click Activate free license to begin the disposable thirty days trial and take away the malicious files.

- HitmanPro will start getting rid of the infected objects.If the program will request you to definitely restart your pc,make sure you allow this request.
Step Six : Reinstate your cutting corners and take away any remaining malicious registry secrets
Recovery has moved your cutting corners files within the Temporary Internet folder and added some malicious registry secrets for your Home windows installation , to revive your files we will have to execute a scan with RogueKiller.
- Please download the most recent official sort of RogueKiller.
ROGUEKILLER DOWNLOAD LINK (This link will instantly download RogueKiller on your pc) - Double click RogueKiller.exe to begin this utility after which wait for a Prescan to accomplish.This will take merely a couple of seconds and you can click on the Start button to carry out a system scan.

- Following the scan has completed, press the Remove button to get rid of any malicious registry secrets.

- Next we will have to reinstate your cutting corners, so click the ShortcutsFix button and permit this program to operate.

STEP 7: Unhide your files and folders
Recovery modifies your file system in a way that files and folders become hidden, to revive the default configurations , it’s important to run the below program.
- Download the Unhide utility, to unhide your files and folders.
UNHIDE.EXE DOWNLOAD LINK (This link will instantly download the Unhide utility on your pc) - Double-click the Unhide.exe icon on your hard drive and permit this program to operate.The entire process shouldn’t take a lot more than ten minutes to accomplish,and also at the finish this utility will produce a report.
STEP 8: Get the desktop think back!
Recovery changes your desktop background to some solid dark colored,to alter it to default one stick to the below instruction.
Original Page: http://malwaretips.com/blogs/file-recovery-virus/
